Manage account security
Manage security requirements for Airship logins and manage user sessions.
If you ever have any security concerns, immediately contact Airship Support .
Managing login and session requirements
Enterprise customers can set security requirements that apply to user accounts that are not enabled for Multi-factor authentication (MFA):
| Requirement | Description |
|---|---|
| Password reset | Password must be reset after 90 days since last password change. |
| Unique password | New password cannot be one of the last three passwords. |
| Block multiple sessions | Ensures that only one session can be active at a time by logging out existing browser sessions upon a new login. |
Company account Owners can manage the requirements:
- Select the account menu icon () in the dashboard header, then select Team Management. If you are in Team Management for Wallet, select the link to go to Team Management for messaging projects, then continue.
- Select Security.
- Enable or disable a requirement.
Managing user sessions
View active web browser sessions for a project’s team members and manually end any session.
To view sessions, select the account menu icon () in the dashboard header, then select Session Management. Sessions are listed with this information:
| Column | Description |
|---|---|
| IP address | The IP address provided by the browser. This may help you verify the network origin of the session. |
| Session start | The date and time when the session began. |
| Session expiry | The date and time when the session will expire. Sessions automatically expire two weeks after they start. |
Select Delete session to manually end a session. Delete a session if you suspect it has been hijacked or a password has been compromised.
Single sign-on (SSO)
Single sign-on (SSO) is a method of authentication where you use one set of credentials to access multiple accounts. If you already use SSO, you may add Airship as another service provider to enable members of your team to access your shared Airship projects without requiring dedicated credentials.
SSO is available for paid Airship pricing plans only. Please contact your account manager or Support to enable this feature if it is not already available for your account.
You must request your user metadata from your identity provider. It must be a standard SP (service provider) metadata XML file . You will upload this file in the steps below.
Configuring a SAML connection
You must configure a new SAML connection for Airship on your identity provider. Include an attribute statement for user email addresses, which Airship uses for authentication. In order for Airship to detect it, the attribute name must be set as http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress, not email or emailaddress alone.
Setting up SSO in Airship
Set up SSO in your Airship project:
- Select the account menu icon () in the dashboard header, then select Team Management. If you are in Team Management for Wallet, select the link to go to Team Management for messaging projects, then continue.
- Select Single Sign-On.
- Under Identity provider (IDP) metadata, select Choose File and upload your metadata file.
- Under Service provider (SP) metadata, select Download SP Metadata.
- Note the Entity ID and Single sign-on web address URLs on this screen. You will use them in later steps.
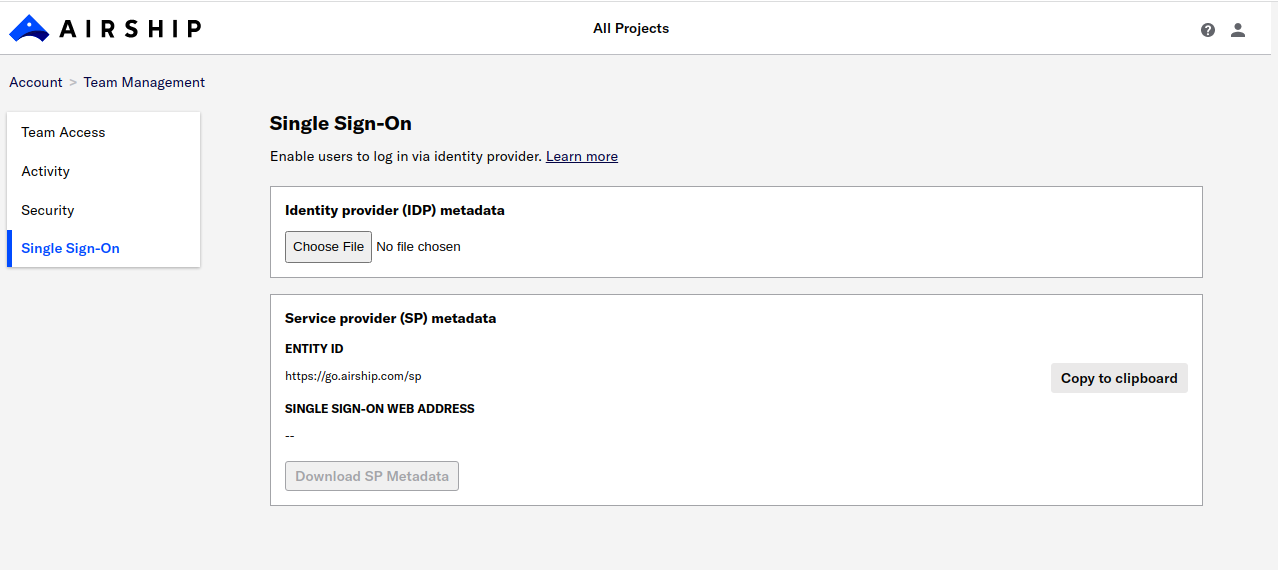
Next, give the SP metadata file to your identity provider, and include the Entity ID URL in case they require it.
Testing SSO
After your identity provider confirms Airship has been set up as a trusted company, have your users go to the Single sign-on web address URL and test SSO login. If logins fail, contact Airship Support or your technical account manager for assistance.
Going live with SSO
Finally, contact Airship Support and tell them SSO login is successful for your company and they can complete setup for you. Support will:
- Set SSO as a requirement for users to access the projects your account
- Invalidate passwords for all users except the account owners and project administrators
- Notify you that SSO configuration is complete
Categories
